overview
Identity and Access Management
Challenge
Identity and Access Management (IAM)
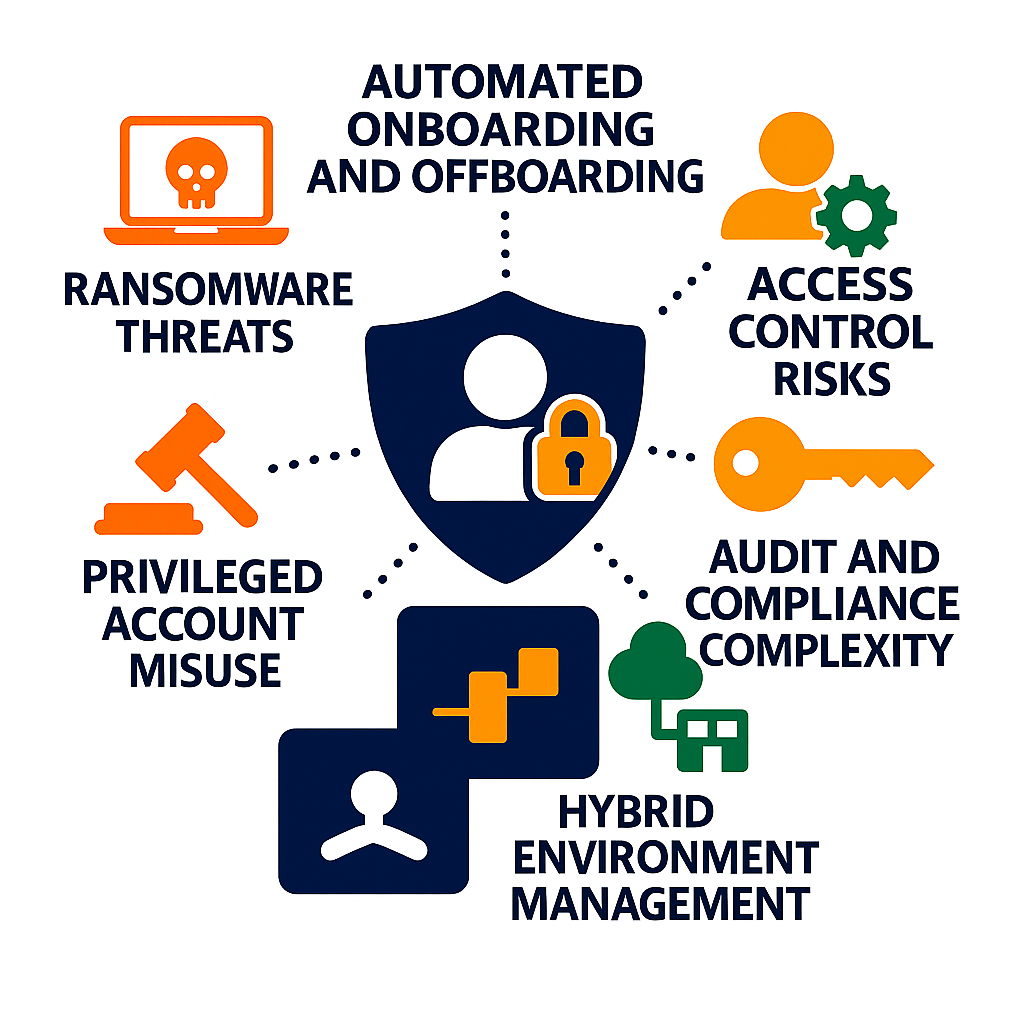
Identity and Access Management (IAM) is crucial for ensuring IT security, compliance, and operational efficiency. However, organizations face several challenges:

Ransomware Threats:
Exploitation of compromised user accounts to propagate ransomware attacks.

Automated Onboarding and Offboarding:
Manual processes for provisioning and de-provisioning users lead to inefficiencies and security risks.

Access Control Risks:
Managing privileged accounts without centralized control increases the risk of unauthorized access.

Privileged Account Misuse:
Difficulty in tracking and controlling administrative access to sensitive systems.

Audit and Compliance Complexity:
Ensuring compliance with regulatory standards like GDPR, HIPAA, and SOX while maintaining audit trails.

Hybrid Environment Management:
Managing users and permissions across on-premises and cloud platforms.

Email Security and Monitoring:
Limited visibility into email activity and potential misuse of resources.
Organizations require advanced IAM solutions to address these challenges and enhance security, compliance, and operational efficiency.
IAM Solutions
How ManageEngine IAM Solutions Can Help
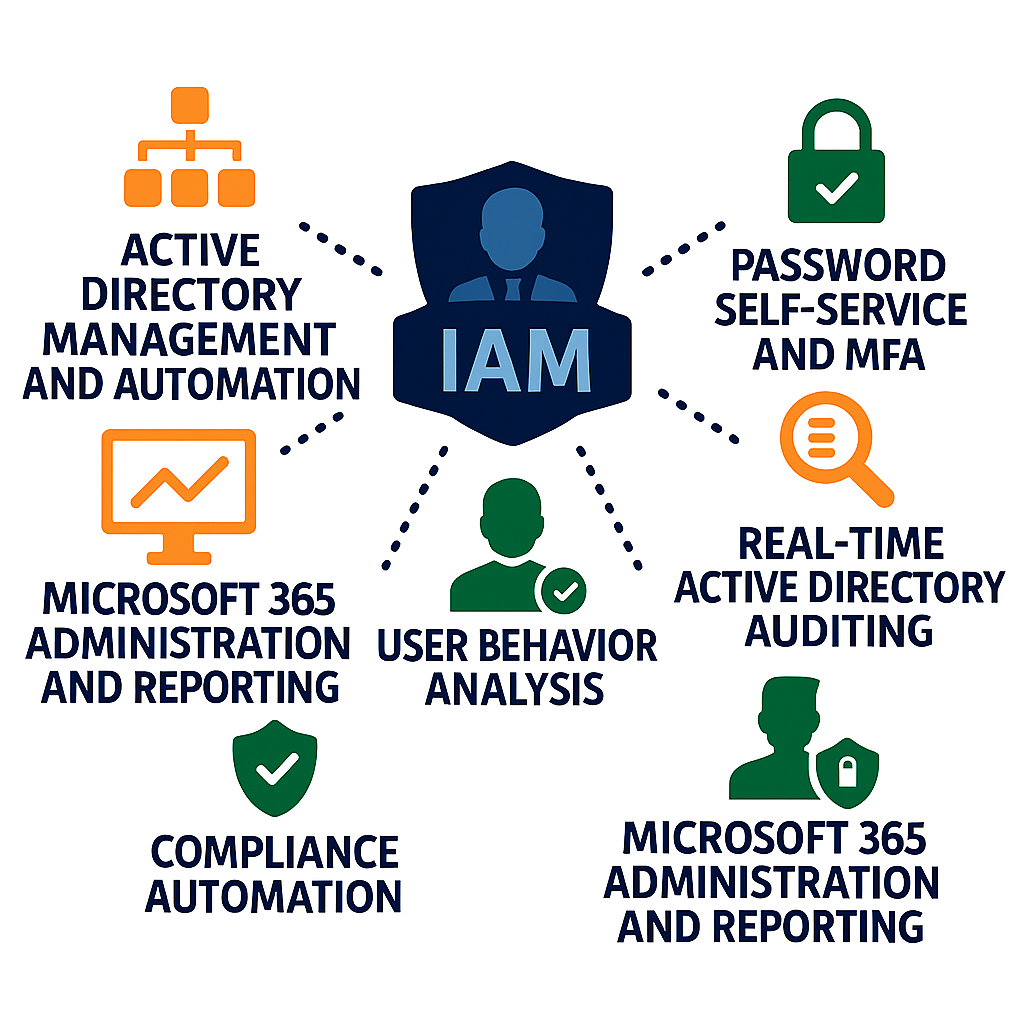
ManageEngine's IAM solutions provide a robust framework for managing identities, access, and security across your IT environment. With AI-driven capabilities and ransomware protection, these solutions help organizations:

Automate onboarding/offboarding:
Automate onboarding/offboarding to eliminate delays and minimize errors.

Proactively detect:
Proactively detect and mitigate ransomware threats.

Centralize privileged:
Centralize privileged account management with PAM360 to enforce strict access control.

Monitor and audit user
Monitor and audit user activities to enhance security and ensure compliance.

Enforce privilege management
Enforce privilege management to control access to sensitive systems.
Ket Features

PAM: Privileged Access Management

Challenges Solved by PAM360:
- Lack of Visibility into Privileged Accounts: PAM360 provides a centralized view of all privileged accounts and their access activities, eliminating blind spots.
- Privileged Credential Sprawl: Consolidates and secures all privileged credentials, reducing the risk of misuse or unauthorized access.
- Inconsistent Session Monitoring: Tracks and records privileged session activities in real-time for auditing and compliance.
- Privileged Account Misuse: Prevents unauthorized access through just-in-time privilege elevation and AI-driven anomaly detection
Ransomware Mitigation: Automatically revoke privileged access when suspicious activity is detected, reducing the impact of ransomware attacks.
Active Directory Management and Automation
- Main Feature: Simplified Active Directory management. Automate user account provisioning, group membership updates, and de-provisioning. AI identifies inactive accounts, predicts group memberships, and recommends cleanup actions for AD optimization.
- Automated Onboarding and Offboarding: Seamless user lifecycle management. Automate account provisioning with predefined role-based access permissions. De-provision user accounts immediately upon employee exit to eliminate security risks.

Password Self-Service and MFA
- Main Feature: Secure self-service password management. Enable users to reset passwords, unlock accounts, and update profiles without IT intervention. Leverage AI to detect unusual login patterns and recommend adaptive MFA enforcement.
- Ransomware Protection: Use anomaly detection to block suspicious login attempts or unauthorized access attempts.
Real-Time Active Directory Auditing
- Main Feature: Real-time monitoring and auditing of user activity. Track logins, permission changes, and object modifications across AD. AI-driven anomaly detection identifies unusual activity, such as privilege escalation or account lockouts, which could indicate ransomware or insider threats.
- Compliance Automation: Generate detailed audit trails for compliance with GDPR, HIPAA, and other standards.
- Ransomware Detection: Monitor and detect unauthorized changes in user accounts or permissions that may signal a ransomware breach.

Microsoft 365 Administration and Reporting
- Main Feature: Comprehensive management of Microsoft 365. Manage users, permissions, licenses, and security settings across Microsoft 365. AI analyzes usage patterns and identifies anomalies such as unusual mailbox activity or unauthorized login attempts.
- Ransomware Protection: Monitor for phishing emails, malicious attachments, and suspicious email patterns to mitigate ransomware risks.

Exchange Server Reporting and Auditing
- Main Feature: Detailed reporting for Exchange environments. Gain insights into mailbox activity, email traffic, and security events. AI detects unusual email patterns, such as spikes in outbound messages or phishing attempts, and alerts administrators.
- Ransomware Detection: Monitor for mass email sending patterns or abnormal data transfers that could indicate ransomware propagation.
AI-Powered Insights and Compliance
- Main Feature: Advanced analytics for security and compliance. AI provides actionable insights into user activity, access patterns, and system changes. Automate compliance reporting for standards like SOX, GDPR, and HIPAA, highlighting potential gaps.

Unified IAM Dashboards
- Main Feature: Centralized visibility and control. Monitor user activities, permissions, and security events across your IT environment. AI correlates data to provide a holistic view of potential threats and compliance status.